Digital authentication system
Electronic authentication - Wikipedia. Other applications Mobile authentication digital authentication system. Mobile authentication is the verification of a users identity through the use a mobile device. E-commerce authentication digital authentication system. In the early 1980s, electronic data interchange (EDI) systems was implemented, which was. Self-sovereign identity. With . See more digital authentication system. What Is Authentication? Definition and Methods. The authentication process includes three primary steps: Identification: Users establish who they are typically through a username digital authentication system. Authentication: Typically, users prove they … digital authentication system. Digital Authentication - the basics - Cryptomathic. The term authentication refers to an electronic process that allows a natural or legal person to be electronically identified. Furthermore, authentication can be used …. Effective Digital Authentication Methods for Cloud and …. Context-aware authentication is the use of contextual information, such as location, time, device, or behavior, to determine the level of trust and access for a user, …
immunocal platinum para que sirve
. Authentication mechanisms | Identification for … digital authentication system. Digital authentication—i.e., authentication that involves electronic credentials and processes—can be done in-person (e.g., at a physical bank branch or government office) … digital authentication system. List of Top Authentication Systems 2023 - TrustRadius digital authentication system. Top Rated Products WatchGuard AuthPoint. AuthPoint Total Identity Security provides businesses with a solution to protect user accounts and. Cisco Duo. Cisco Duo is a two …. What are the most common digital authentication methods?. Digital authentication is the process of verifying that users or devices are who or what they claim to be in order to enable access to sensitive …. Authentication - Wikipedia. Authentication (from Greek: αὐθεντικός authentikos, "real, genuine", from αὐθέντης authentes, "author") is the act of proving an assertion, such as the identity of a computer …. Digital ID: A key to inclusive growth | McKinseytrgool
. Digital identification, or “digital ID,” can be authenticated unambiguously through a digital channel, unlocking access to banking, government benefits, education, and many other critical services. The …. What Is Authentication And How Does It Work? - Forbes. What is authentication? Generally speaking, authentication is a term that refers to the process of proving that some fact or some document is genuine. The term … digital authentication system. How governments can deliver on the promise of digital ID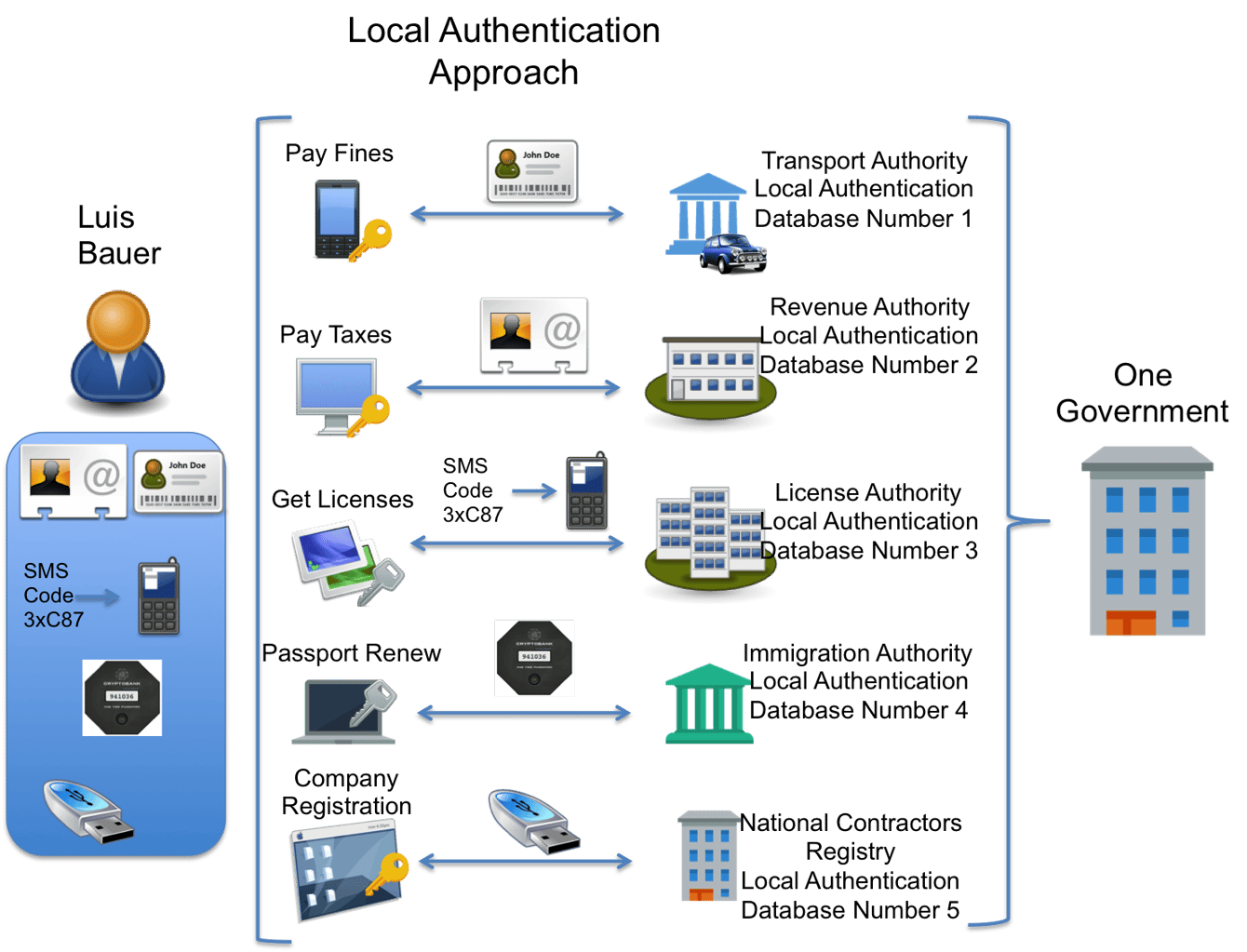
παυλακησ ζαχαροπλαστειο
. SP 800-63 is a suite of four documents: SP 800-63-3 (the parent document; your starting point for all things digital …
kak anie shellrock
. Digital identification, or “digital ID,” can be authenticated unambiguously through a digital channel, unlocking access to banking, government benefits, education, and many other critical services. The …. National e-Registration/Authentication Service | Ministry of .. E-Authentication Service acts as a national identity provider for all government online services digital authentication systembulud kimi doluyam men
. It provides secure authentication, digital signing and Single-Sign-On (SSO) services and is a key component in e-services development and securityπως μπορω να δω ποιοι ειναι συνδεδεμενοι στο ρουτερ μου
. It delivers improved security, usability and efficiency for end-users of government e-services.. Best Identity Verification Software in 2023: Compare …
siki necə boyutmek olar
. Save to My Lists. Overview. User Satisfaction. Product Description. Trulioo is a global identity verification company building … digital authentication system. Best identity management software of 2023 | TechRadar. OneLogin is a cloud-based authentication system that makes it easier for firms to secure their digital assets and users. It can handle multiple applications at once and has single sign-on .. Authentication mechanisms | Identification for Development. Digital authentication via a 2D barcode: Cards, certificates, or mobile apps with 2D barcodes (e.g., QR codes) . In 2016, the UK government launched its GOV.UK Verify system to provide a digital identity layer that would allow UK citizens and residents to authenticate themselves online for a variety of public and private sector services. digital authentication system. Authentication: Definition, Types, Uses & More | StrongDMkızlığı bozulduğu biri nasıl anlaşılır
. A digital certificate, also known as a public-key certificate, is an electronic document that stores the public key data, including information about the key, its owner, and the digital signature verifying the identity. CBA is often used as part of a two-factor or multi-factor authentication process.. Digital Identity Guidelines - NIST. given system. The components of identity assurance detailed in these guidelines are as follows: • IALpizza fan 50% έκπτωση
. refers to the identity proofing process. • AAL. refers to the authentication process. • FAL. refers to the strength of an assertion in a federated environment, used to communicate authentication and attribute information (if applicable .. Processes | Free Full-Text | Dynamic Signature Verification. Biometric systems input physical or personal human characteristics for identification, authentication, and security purposes digital authentication system. With the advancement in communication and intelligent security systems, biometrics are programmed to validate electronic signatures (E-signatures) for online and offline authentication. This article …. What is Authentication? | Webopediapozdrawiam po angielsku
. With a passwordless authentication system, users don’t have to enter a code or passphrase to log in digital authentication system. Instead, they can use biometric measures (fingerprints, face scans) or digital means (tokens or cookies) to gain access. These systems require minimal effort on the user’s part and offer more privacy than other authentication methods.. Advantages & Disadvantages of Authentication Systems | Mitek. The number of people needing to transmute physical identity credentials into digital identities has skyrocketed, increasing the importance of strong authentication. In the whitepaper Future of Identity 2.0, Mitek’s CTO, Steve Ritter, outlines six significant identity-related change vectors that have sharply increased in velocity since the …. Blockchain-based identity management systems: A review. a system for identity and access management using blockchain technology to support authentication and authorization of entities in a digital system. poor scalability, performance doesnt meet requirement. A simulation based on Hyperledger Fabric was made, achieved in a decentralized, efficient, and secure manner. digital authentication system. Quick Guide to Electronic Verification System (eVS®) | PostalPro. Quick Guide to Electronic Verification System (eVS®) This document provides short, digestible information on Electronic Verification System (eVS). October 08, 2020. Download. Feedback.. What is Authentication? | Definition from TechTarget. authentication ticket or ticket-granting ticket (TGT): An authentication ticket, also known as a ticket-granting ticket (TGT), is a small amount of encrypted data that is issued by a server in the Kerberos authentication model to begin the authentication process digital authentication system. When the client receives an authentication ticket, the client sends the ticket .. NIST Special Publication 800-63B. This technical guideline applies to digital authentication of subjects to systems over a network. It does not address the authentication of a person for physical access (e.g., to a building), though some credentials used for digital access may also be used for physical access authentication.. The Benefits of Digital Identity Verification - Juniper Research digital authentication system. The ID verification market is witnessing a consumer paradigm shift from manual identity verification systems to those based on electronic credentials. Due to the COVID-19 pandemic, 2020 became the ‘year of change’ where expectations around identity verification in a digital environment accelerated.. sang hoki29.heti lottószámok
al assi
الرد على احسن الله عزاكم في الإمارات
鐵將縱橫吧
syair 2d
ramalan cuaca di kuala pilah
good manner kf94
lavanda prahoveana
escort girl tbilisi